
Say you’ve just built your application and for the data layer, you’ve chosen to deploy MongoDB on AWS EC2 instances that you will manage yourself. Pause for a moment and consider your self-managed MongoDB instances over the lifetime of your application. Now ask yourself these questions:
- Who will keep our database operating system up to date?
- Who will ensure the database software is recent?
- Who is supposed to configure network security for the database?
- Who will buy, install, maintain and rotate our SSL certificates?
- Who will ensure user accounts are properly managed over time?
- Who will encrypt our data at rest?
If you don't really have answers for these questions, or, if your answer for these questions points to just one person, maybe it's time to consider a service that will do all of these things for you. When we approached the task of building MongoDB Atlas, our database as a service, our engineers made security a top priority. By hosting your data in the cloud with MongoDB Atlas, you can leverage the security best practices that are part of MongoDB Atlas.
Let's talk individually about the security features built into the MongoDB Atlas service.
Access Control, Always.
MongoDB Atlas has username and password based authorization and authentication enabled, always. MongoDB Atlas makes use of SCRAM-SHA-1 as it's default authentication mechanism, which is part of the MongoDB database core. It follows the IETF standard, RFC 5802, that defines best practice methods for implementation of challenge-response mechanisms for authenticating users with passwords.
You can use a variety of predefined user roles such as "Atlas admin" which is essentially a full rights, administration user, "Read and write to any database", which permits no administrative rights, or "Only read any database", which allows you read-only access.

You also have the ability to define permissions for any specific user, i.e. : 1) what databases they can access and 2) what they’re authorized to do. I am creating a custom user account named "mdbuser" that can only perform reads and writes to one database, named "MyData”.
TLS/SSL Encryption by Default
MongoDB Atlas utilizes TLS/SSL to encrypt connections to your database. You can trust your data will be transmitted from endpoint to endpoint without concern thanks to this default configuration. All connections to your database, either from your shell or from your app, are encrypted using the TLS/SSL. All replication connections from your primary replica set member to your secondary MongoDB nodes in your cluster are also protected
Disk Encryption
MongoDB Atlas clusters on AWS make use of the General Purpose SSD (gp2) EBS volumes, which include support for AES-256 encryption. MongoDB Atlas makes encrypting your data at rest simple by allowing you to just point and click from the management GUI to encrypt your persistent storage

You can select disk encryption either at creation time, or just go to the configuration section of your cluster and add it later.
Secure from the network
Password authentication and authorization are important controls, but it's difficult to compromise a database if you cannot connect to it at all.
By default, all MongoDB Atlas databases have no IP address entries permitted in the security whitelist. This means the database will never simply listen to the internet without a password. To permit our application to connect to our data, we can specify inbound network connections via our IP whitelist.
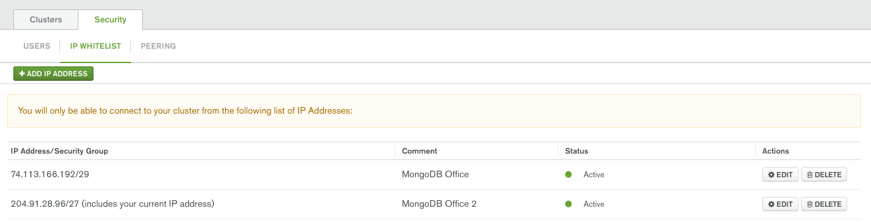
You can add IPs via the control panel as shown above, or modify entries using the Atlas API.
VPC Peering
If you are using Amazon Web Services, you can peer your VPC (Virtual Private Cloud) where your AWS resources live to your MongoDB Atlas cluster VPC. This permits you to further reduce your risk profile by only permitting access to your data from private IP addresses on the AWS network, or via your security groups.
You can use native security group names from AWS or simply enter the CIDR annotation of the servers in your VPC you would like to connect to your Atlas cluster. For a full tutorial on how to implement VPC peering with your Atlas cluster, you can review this YouTube video, along with many other tutorials on using MongoDB Atlas features.
Automated Updates
MongoDB Atlas will always be running with the latest security fixes for your MongoDB database cluster. Updates and minor version database upgrades to your cluster are performed by us with no manual intervention from you, and no downtime. It’s all handled via automation agents, which report back to our engineers if any issues occur during the upgrade process, allowing our team of experts to monitor, review, and quickly rectify any potential problems.

Information on deployed upgrades to your cluster can be found by going to the "Activity Log" on your MongoDB Atlas Cluster in the Alerts section of the management GUI.
End to End Security in the Cloud
MongoDB offers some of the most sophisticated security controls of any modern database. MongoDB Atlas makes it simpler to reduce risk by having these controls built in and available to any cloud deployment. This approach allows you to concentrate on code, and spend less time managing security protection.
For more information, check out our downloadable guide on MongoDB Atlas security controls.