We’re excited to announce the general availability of Google Cloud Private Service Connect (PSC) as a new network access management option in MongoDB Atlas. Announced alongside the availability of MongoDB 5.1, Google Cloud PSC is GA for use with Altas. See the documentation for instructions on setting up Google Cloud PSC for Atlas, or read on for more information.
MongoDB Atlas is secure by default. All dedicated Google Cloud clusters on Atlas are deployed in their own VPC. To set up network security controls, Atlas customers already have the options of an IP Access List and VPC Peering.
-
The IP Access List in Atlas is a straightforward and secure connection mechanism, and all traffic is encrypted with end-to-end TLS. But you must be able to provide static public IPs for your application servers to connect to Atlas, and to list those IPs in the Access List. If your applications don’t have static public IPs or if you have strict requirements on outbound database access via public IPs, this won’t work for you.
-
The existing solution to this is VPC Peering, which allows you to configure a secure peering connection between your Atlas cluster’s VPC and your own Google Cloud VPC(s). This is easy, but the connections are two way. Atlas never has to initiate connections to your environment, but some Atlas users don’t want to use VPC peering because it extends the perceived network trust boundary. Access Control Lists (ACLs) and IAM Groups can control this access, but they require additional configuration.
MongoDB Atlas and Google Cloud PSC
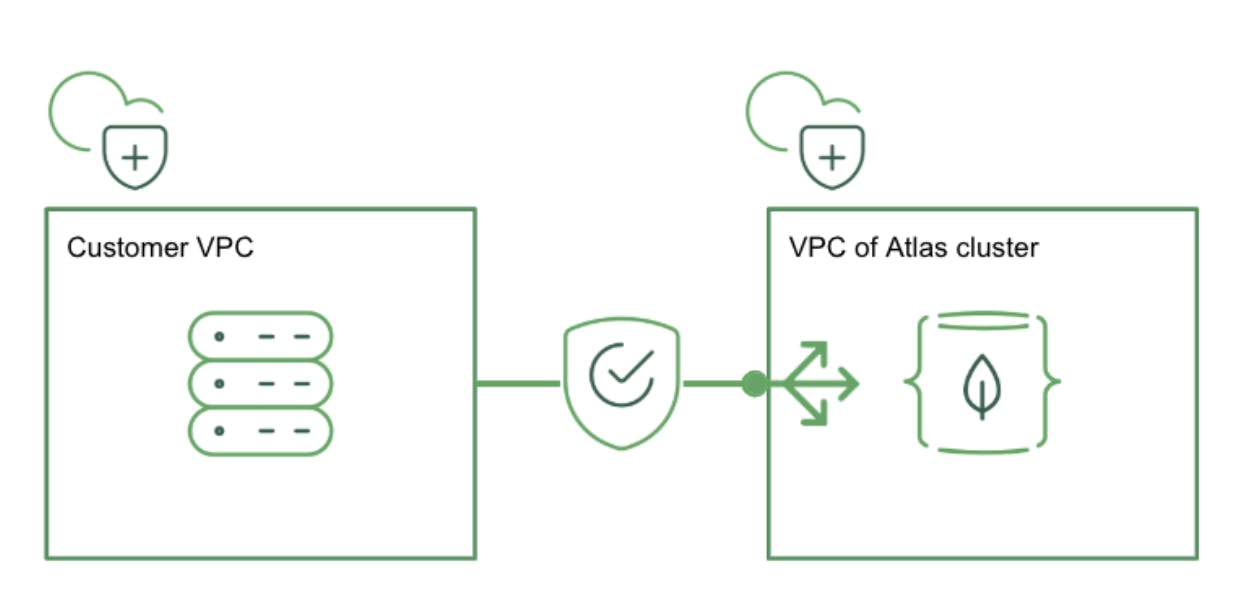
Now, you can use Google Cloud Private Service Connect to connect a VPC to MongoDB Atlas. Private Service Connect allows you to create private and secure connections from your Google Cloud networks to MongoDB Atlas. It creates service endpoints in your VPCs that provide private connectivity and policy enforcement, allowing you to easily control network security in one place.
This brings two major advantages:
-
Unidirectional: connections via PSC use a private IP within the customer’s VPC, and are unidirectional. Atlas cannot initiate connections back to the customer's VPC. This means that there is no extension of the perceived network trust boundary.
-
Transitive: connections to the PSC private IPs within the customer’s VPC can come transitively from an on-prem data center connected to the PSC-enabled VPC with Cloud VPN . Customers can connect directly from their on-prem data centers to Atlas without using public IP Access Lists.
Meeting security requirements with Atlas on Google Cloud
Google Cloud PSC adds to the security capabilities that are already available in MongoDB Atlas, like Client Side Field-Level Encryption, database auditing, BYO key encryption with Google Cloud KMS integration, federated identity, and more. MongoDB Atlas undergoes independent verification of security and compliance controls, so you can be confident in using Atlas on Google Cloud for your most critical workloads.
To learn more about configuring Google PSC with MongoDB Atlas, visit our docs. If you’re already managing your Atlas clusters with our API, you can add a private endpoint with the documentation here.
For more information about Google Cloud Private Service Connect, visit the Google Cloud docs or read the Introducing Private Service Connect release announcement.
Try MongoDB Atlas for free today!